-
TOR
Surf the Internet without leaving traces

The TOR website is: https://www.torproject.org/
Using TOR and Firefox ver.12 - Update April 2012
Using TOR - May 2010
How to test your installation
-
Using TOR - April 2012
For using TOR on Ubuntu 10.04 with Firefox (v.12) are necessary.
-
Using TOR - May 2010
For using TOR on Ubuntu 10.04 with Firefox are necessary.
Follow the instructions below.
Using TOR and Firefox ver.12 - Update April 2012
Using TOR - May 2010
How to test your installation
-
Using TOR - April 2012
For using TOR on Ubuntu 10.04 with Firefox (v.12) are necessary.
- Download the TOR SW from this website: https://www.torproject.org/
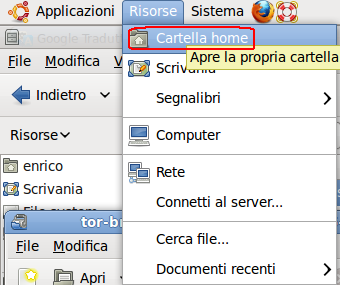
- Now open: Risorse -> Cartella Home (see below)
- Now go in the directory where you have saved TOR and double click on it to unboxing it (see below).
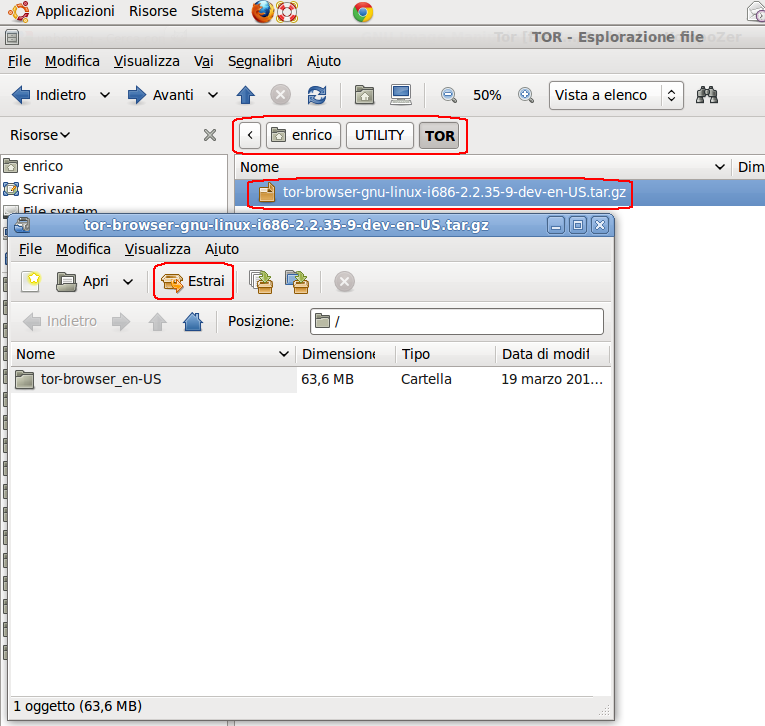
Now you have something like this:
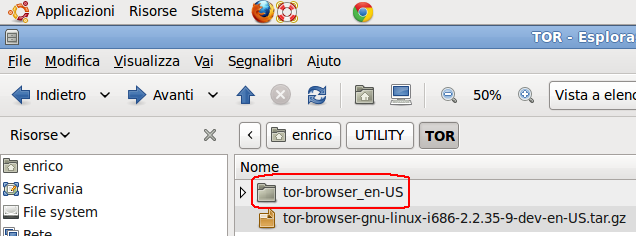
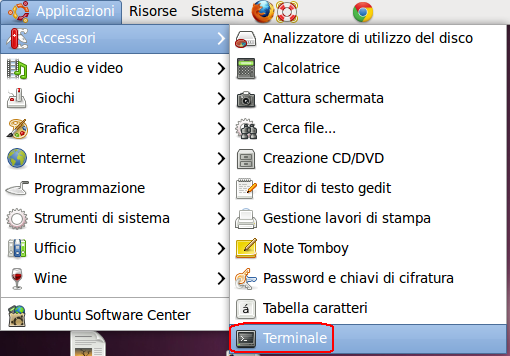
- Now open a TERMINAL (see below)

- Now go in the directory where you have unzipped TOR.
For do this use the command:
cd DirectoryName
In my case the directory is .../UTILITY/TOR/tor-browser_en-US
so the cd command is:
cd UTILITY/TOR/tor-browser_en-US
See below.
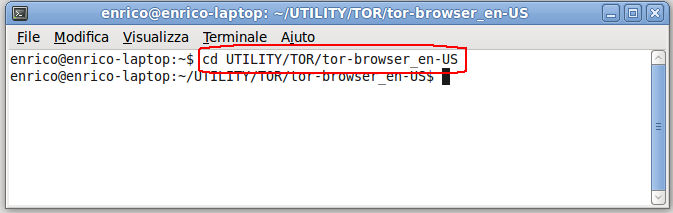
- Now type the command:
./start-tor-browser
and after 20...30 sec will appear the window below.
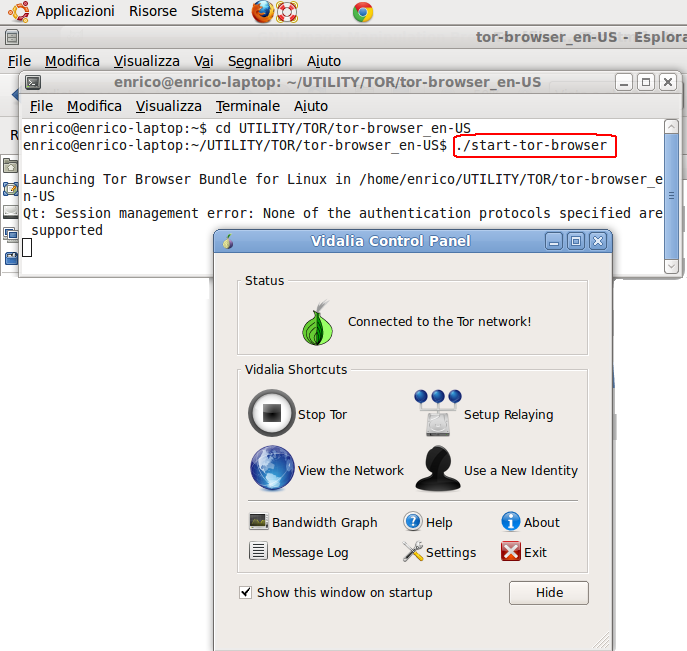
- After some second will appear the window below
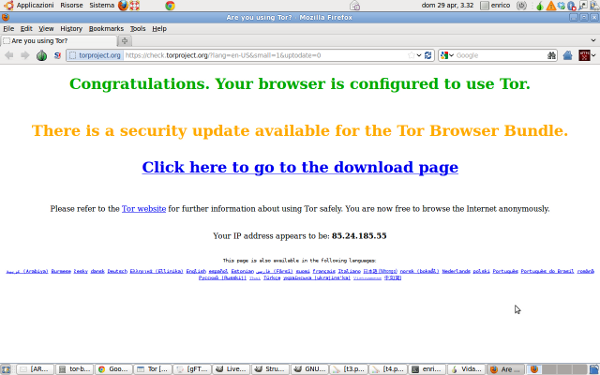
Now you are ready to surf the Internet without leaving traces.
ATTENTION: do not close the Terminal, if you close the terminal you KILL the TOR.
-
Using TOR - May 2010
For using TOR on Ubuntu 10.04 with Firefox are necessary.
1) TOR sw
2) POLIPO sw
2) POLIPO sw
Follow the instructions below.
- Installing TOR sw, for do this follow the lines below
- Open a TERMINAL and write:
sudo su
(login for the SuperUser)
- Add the new repository in the fiele: /etc/apt/sources.list, for do this write:
cd /etc/apt
gedit sources.list
at the end of file add the line:
deb http://deb.torproject.org/torproject.org lucid main
(lucid is because I'm using UBUNTU 10.04, if you using UNUNTU 9.10 using karmic and so on.) - Save and close gedit.
From the Terminal add the key by writing:
gpg --keyserver keys.gnupg.net --recv 886DDD89
gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add - - now update the sostware resource and install TOR. For do this write:
apt-get update
apt-get install tor tor-geoipdb
- Install and configuring POLIPO sw
- From Applicazioni select Ubuntu Software Center and search and install Polipo
- After the Polipo installation open the file: /etc/polipo/config for do this write:
cd /etc/polipo
gedit config
and replace the contents with the follow lines and save it
### Basic configuration
### *******************
# Uncomment one of these if you want to allow remote clients to
# connect:
# proxyAddress = "::0" # both IPv4 and IPv6
# proxyAddress = "0.0.0.0" # IPv4 only
proxyAddress = "127.0.0.1"
proxyPort = 8118
# If you do that, you'll want to restrict the set of hosts allowed to
# connect:
# allowedClients = "127.0.0.1, 134.157.168.57"
# allowedClients = "127.0.0.1, 134.157.168.0/24"
allowedClients = 127.0.0.1
allowedPorts = 1-65535
# Uncomment this if you want your Polipo to identify itself by
# something else than the host name:
proxyName = "localhost"
# Uncomment this if there's only one user using this instance of Polipo:
cacheIsShared = false
# Uncomment this if you want to use a parent proxy:
# parentProxy = "squid.example.org:3128"
# Uncomment this if you want to use a parent SOCKS proxy:
socksParentProxy = "localhost:9050"
socksProxyType = socks5
### Memory
### ******
# Uncomment this if you want Polipo to use a ridiculously small amount
# of memory (a hundred C-64 worth or so):
# chunkHighMark = 819200
# objectHighMark = 128
# Uncomment this if you've got plenty of memory:
# chunkHighMark = 50331648
# objectHighMark = 16384
chunkHighMark = 67108864
### On-disk data
### ************
# Uncomment this if you want to disable the on-disk cache:
diskCacheRoot = ""
# Uncomment this if you want to put the on-disk cache in a
# non-standard location:
# diskCacheRoot = "~/.polipo-cache/"
# Uncomment this if you want to disable the local web server:
localDocumentRoot = ""
# Uncomment this if you want to enable the pages under /polipo/index?
# and /polipo/servers?. This is a serious privacy leak if your proxy
# is shared.
# disableIndexing = false
# disableServersList = false
disableLocalInterface = true
disableConfiguration = true
### Domain Name System
### ******************
# Uncomment this if you want to contact IPv4 hosts only (and make DNS
# queries somewhat faster):
#
# dnsQueryIPv6 = no
# Uncomment this if you want Polipo to prefer IPv4 to IPv6 for
# double-stack hosts:
#
# dnsQueryIPv6 = reluctantly
# Uncomment this to disable Polipo's DNS resolver and use the system's
# default resolver instead. If you do that, Polipo will freeze during
# every DNS query:
dnsUseGethostbyname = yes
### HTTP
### ****
# Uncomment this if you want to enable detection of proxy loops.
# This will cause your hostname (or whatever you put into proxyName
# above) to be included in every request:
disableVia = true
# Uncomment this if you want to slightly reduce the amount of
# information that you leak about yourself:
# censoredHeaders = from, accept-language
# censorReferer = maybe
censoredHeaders = from,accept-language,x-pad,link
censorReferer = maybe
# Uncomment this if you're paranoid. This will break a lot of sites,
# though:
# censoredHeaders = set-cookie, cookie, cookie2, from, accept-language
# censorReferer = true
# Uncomment this if you want to use Poor Man's Multiplexing; increase
# the sizes if you're on a fast line. They should each amount to a few
# seconds' worth of transfer; if pmmSize is small, you'll want
# pmmFirstSize to be larger.
# Note that PMM is somewhat unreliable.
# pmmFirstSize = 16384
# pmmSize = 8192
# Uncomment this if your user-agent does something reasonable with
# Warning headers (most don't):
# relaxTransparency = maybe
# Uncomment this if you never want to revalidate instances for which
# data is available (this is not a good idea):
# relaxTransparency = yes
# Uncomment this if you have no network:
# proxyOffline = yes
# Uncomment this if you want to avoid revalidating instances with a
# Vary header (this is not a good idea):
# mindlesslyCacheVary = true
# Suggestions from Incognito configuration
maxConnectionAge = 5m
maxConnectionRequests = 120
serverMaxSlots = 8
serverSlots = 2
tunnelAllowedPorts = 1-65535 - Now restart your PC
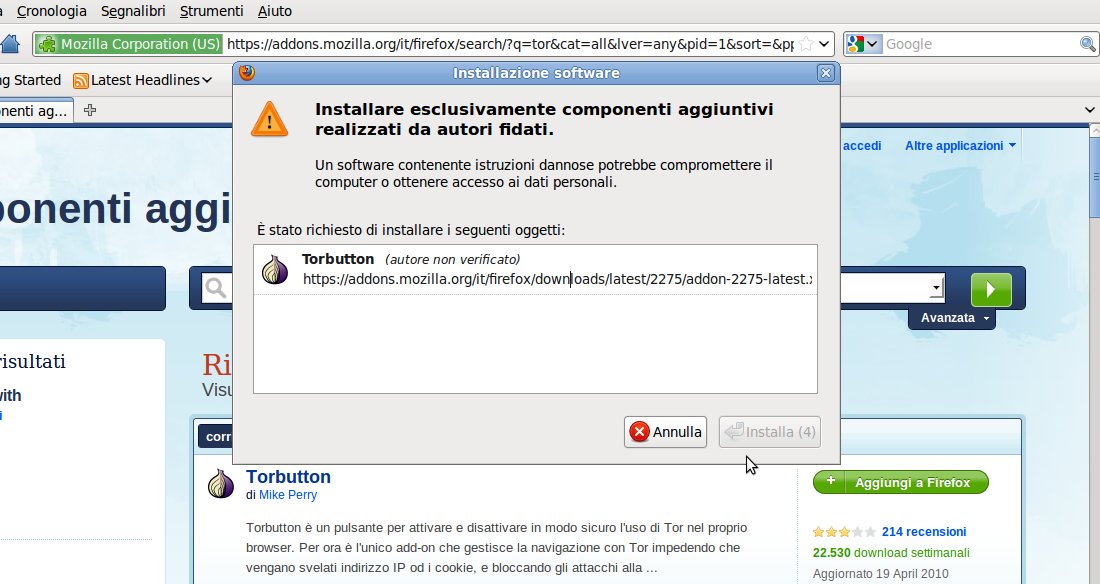
- The last thing to do is to configure the Tor button in Firefox.
For do this click here and search and istall the Tor button (write TOR)
- Now for using Firefox with TOR is necessary press TOR icon on the Firefox (look right and down)
-
For testing TOR use this sequence:
- Open Firefox with TOR disable and go to this address:
http://www.indirizzo-ip.com/
and annotate your IP-Address - Now Open a new Firefox and ENABLE TOR and go again at the address:
http://www.indirizzo-ip.com/
your IP-Address is changed, this means that your TOR is working